Top 5 Cyber Risks for Businesses
Cyber attacks continue to grow, with cyber thieves in pursuit of personally identifiable data that can be sold on the black market. According to the 2015 Symantec Internet Security Threat report, the past year saw a 23% increase in the number of data breaches.
Learn about some of the top cyber risks and what they may mean for your business, regardless of size. These sample scenarios illuminate the five top cyber risks for businesses and can help demonstrate what can happen to a company as a result of these vulnerabilities.
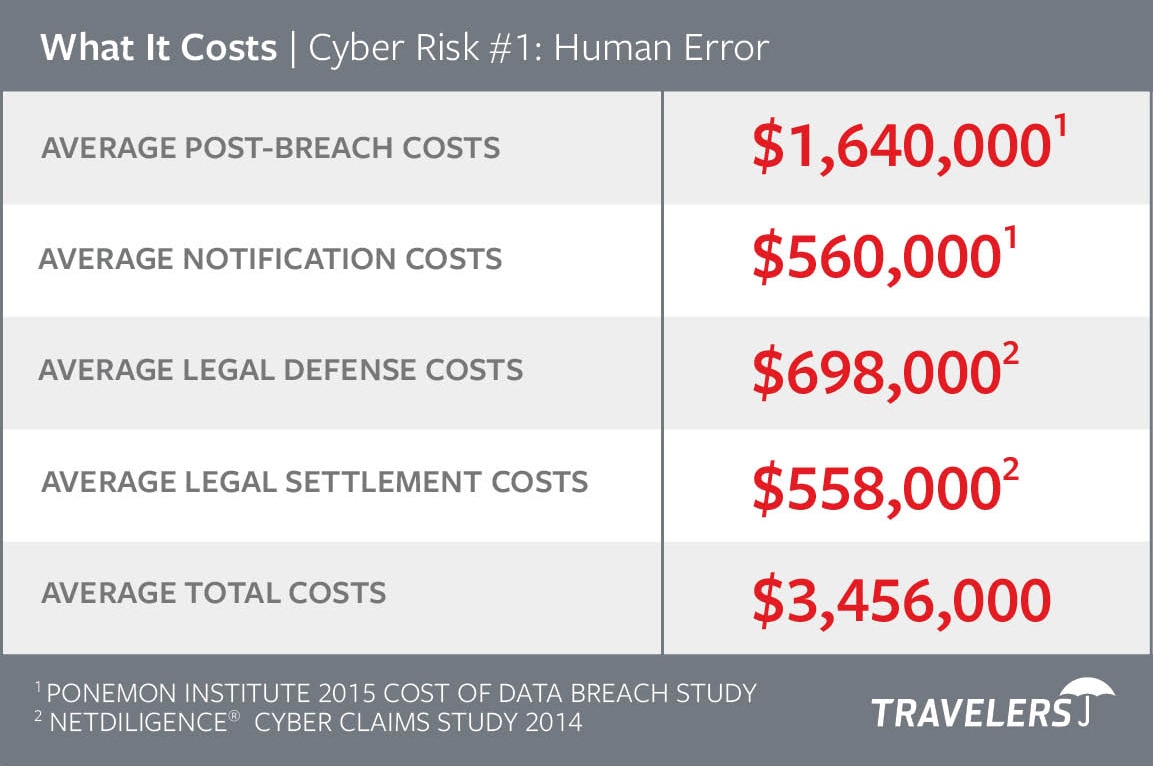
Cyber Risk #1: Human Error: Lost and Stolen Laptops and Smartphones
Company Profile: Professional Services | $40 Million Annual Revenue
What happens when an employee loses a smartphone with sensitive computer data?
In this example, an administrator at an employee benefits company lost his personal smartphone, which he used to access an unsecured database containing the records of more than 15,000 clients, including social security numbers and private health information.
- Losing the device resulted in costs for legal services, a forensic investigation and miscellaneous expenses.
- In addition to data breach notification and remediation costs, it also cost the company one of its largest clients.
- Several other clients are considering legal action against the firm for failing to prevent unauthorized access to electronic data containing confidential information of others.
Cyber Risk #2: Hacker
Company Profile: Retail | $5 Billion Annual Revenue
How does an attack on a major retailer’s point of sale system affect business?
In this example, a hacker attacked the retailer’s point of sale system, which meant a certified forensic examiner was required to conduct a forensic audit of the entire point of sale system. The retailer also hired a law firm to serve as counsel and breach coach.
- The retailer had to pay to notify its 20 million customers that their personal information was compromised in the incident.
- Other costly protection included providing ongoing credit monitoring.
- A number of class action lawsuits were filed and are still pending.
Cyber Risk #3: Spear Phishing: Social Engineering Targeted at Employees
Company Profile: Business Services | $100 Million Annual Retail
How does an innocent-looking email lead to online banking fraud?
After the office manager of a firm opened an email that appeared to contain an invoice, the firm’s online banking account was commandeered. Clicking on the Trojan horse email triggered a computer virus that allowed criminals to disable security measures, including transfer verification emails.
- The office manager did not receive emails that would have informed the firm about wire transfers.
- The criminals then sent 26 wire transfers of $25,000 each to 20 individuals and small businesses around the world.
Cyber Risk #4: Extortion
Company Profile: Construction | $10 million Annual Revenue
How can extortion by a rogue employee affect business?
In this example, a rogue employee gained access to a construction firm’s data system through an SQL injection and attempted to extort money in exchange for restoring essential project files. When the firm refused to pay, the employee threatened to destroy the files, which would have been catastrophic due to lack of an adequate backup system.
- After hiring a forensic IT expert, the firm was able to identify the employee and restore the files.
- There was a significant business interruption.
- The firm had to hire a crisis PR coach to explain missing a major project deadline.
Cyber Risk #5: Hacktivism: Social and Political “Hactivists”
Company Profile: Hospitality | $700 Million Annual Revenue
What happens when weak encryption allows an international hacktivist to access an American hotel’s customer database?
More than 30,000 sensitive records, including credit card data and social security numbers, were exposed. The hotel pledged to do everything it could to protect its guests, but was surprised to learn what a breach this size could cost.
- The hotel had to pay significant notification and remediation costs.
- Regulators investigated the hotel’s cyber breach policies, which added considerable time and cost.
- Restoring the hotel’s reputation required investing in a complete rebranding campaign.