Target Data Breach Insurance Case Study - By Christine Marciano
Learning from Target: Insurance Coverage For Data Breaches by Alex Purvis
Cyber liability is a clear and present danger. Target Corp. recently reported at least $235 million as gross expenses related to its 2013 data breach. Fortunately, Target was able to recover $90 million of that loss under insurance coverage dedicated to cyber liability.
Target's experience is the most recent wake-up call on this front, and business executives should be evaluating what protection they have against this potentially enormous risk, one that can rear its head in many forms (e.g., laptop loss, hacking, and employee theft). A significant piece of that risk analysis should include consideration of available insurance coverage.
Insurance protection for cyber risks may be available in one of two forms. First, cyber liability policies are becoming available on the market and can offer a tailored layer of protection. Second, coverage may be available under more traditional insurance products (e.g., Commercial General Liability ("CGL"), Directors & Officers ("D&O"), or crime/fidelity policies).
Cyber Coverage
Now is the time to start considering cyber coverage if your business does not already have it. There are numerous forms available in an ever-changing market, and the industry is designing these products to address the unique risks that arise in this context. For example, one of the largest risks related to cyber liability is exposure to regulatory investigations and inquiries. Insurers on traditional policies may argue that the costs of a regulatory investigation are not covered, and a cyber liability policy should provide more certainty on that issue. Insurance professionals can provide access to the various markets and advice on the differences between certain products.
If evaluating cyber coverage, keep in mind that care in the application process may be critical. Most cyber insurers will ask a series of detailed questions about the current status of your data protection system, and it is important to read and answer these questions with caution. Many of the cyber policies will include harsh exclusions related to any perceived misrepresentation in the application process, and most experts anticipate the industry may rely heavily upon these exclusions in the face of future claims. The cyber policy you pay for may prove worthless if questions later emerge about the veracity of the underwriting process, so make sure all questions are understood and answered correctly.
There should also be room for negotiation on these policies. As always, reading the policy form before agreeing to it is critical, and any questions should be raised up front. The offering insurers or their agents should provide clarification relative to any ambiguities, and clarifying endorsements may be particularly helpful on these new products.
There will certainly be coverage fights as cyber policies start responding to claims, and the courts will need to provide direction and clarification. That said, any company with concerns about data breach exposure should explore these products.
Coverage Under Traditional Policies
Many businesses will face a data breach loss without cyber coverage and may wonder whether all is lost. Fortunately, some more traditional insurance may provide coverage for data breaches, and there is a developing body of case law that provides some guidance. For example, in Retail Systems, Inc. v. CNA Insurance Companies, the Minnesota Court of Appeals held that an insured's loss of a computer tape containing third-party data constituted "property damage" under the standard CGL definition. As another example, CGL policies typically provide coverage for invasion of privacy, and the Ninth Circuit, inNetscape v. Federal Insurance Company, applied that language to find coverage for Netscape related to allegations that it was employing software that improperly collected user information. Other courts have examined similar issues and have denied coverage based on interpretations of the relevant policy language.
Most importantly, your business's current insurance portfolio should be carefully considered in the event of a loss. Even policies that you might not expect to provide coverage could be responsive to the claim. Notice should be provided to any potentially applicable policies, and any coverage denials should be given scrutiny by someone with coverage experience on your side of the issue.
Finally, be aware of the recent endorsements being offered by the Insurance Services Office ("ISO"). The industry is unlikely to admit that prior traditional policy forms are unclear in any way, but ISO has obtained approval in almost every state for a series of endorsements that seek to expressly exclude any coverage for cyber liability under traditional policy forms. Courts will need to interpret these endorsements over time, but policyholders should be given an opportunity to have a complete understanding of their impact before agreeing to add them to their policies. If presented with anything that looks like an exclusionary endorsement, ask questions of your insurance professional.
Conclusion
The takeaway here is that cyber liability can no longer be ignored. Insurance coverage for this threat is an important part of any risk management plan. If your business has not yet suffered a loss, consider protection for the future. If you have suffered a loss, determine what protection you may already have and consider strengthening your cyber coverage.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.
Source https://www.mondaq.com/unitedstates/x/339134/data+protection/Learning+from+Target+Insurance+Coverage+for+Data+Breaches
Cards Stolen in Target Breach Flood Underground Markets.
Credit and debit card accounts stolen in a recent data breach at retail giant Target have been flooding underground black markets in recent weeks, selling in batches of one million cards and going for anywhere from $20 to more than $100 per card, KrebsOnSecurity has learned.
Prior to breaking the story of the Target breach on Wednesday, Dec. 18, I spoke with a fraud analyst at a major bank who said his team had independently confirmed that Target had been breached after buying a huge chunk of the bank’s card accounts from a well-known “card shop” — an online store advertised in cybercrime forums as a place where thieves can reliably buy stolen credit and debit cards.
There are literally hundreds of these shady stores selling stolen credit and debit cards from virtually every bank and country. But this store has earned a special reputation for selling quality “dumps,” data stolen from the magnetic stripe on the backs of credit and debit cards. Armed with that information, thieves can effectively clone the cards and use them in stores. If the dumps are from debit cards and the thieves also have access to the PINs for those cards, they can use the cloned cards at ATMs to pull cash out of the victim’s bank account.
At least two sources at major banks said they’d heard from the credit card companies: More than a million of their cards were thought to have been compromised in the Target breach. One of those institutions noticed that one card shop in particular had recently alerted its loyal customers about a huge new batch of more than a million quality dumps that had been added to the online store. Suspecting that the advertised cache of new dumps were actually stolen in the Target breach, fraud investigators with the bank browsed this card shop’s wares and effectively bought back hundreds of the bank’s own cards.
When the bank examined the common point of purchase among all the dumps it had bought from the shady card shop, it found that all of them had been used in Target stores nationwide between Nov. 27 and Dec. 15. Subsequent buys of new cards added to that same shop returned the same result.
On Dec. 19, Target would confirm that crooks had stolen 40 million debit and credit cards from stores nationwide in a breach that extended from Nov. 27 to Dec. 15. Not long after that announcement, I pinged a source at a small community bank in New England to see whether his institution had been notified by Visa or MasterCard about specific cards that were potentially compromised in the Target breach.
This institution has issued a grand total of more than 120,000 debit and credit cards to its customers, but my source told me the tiny bank had not yet heard anything from the card associations about specific cards that might have been compromised as a result of the Target breach. My source was anxious to determine how many of the bank’s cards were most at risk of being used for fraud, and how many should be proactively canceled and re-issued to customers. The bank wasn’t exactly chomping at the bit to re-issue the cards; that process costs around $3 to $5 per card, but more importantly it didn’t want to unnecessarily re-issue cards at a time when many of its customers would be racing around to buy last-minute Christmas gifts and traveling for the holidays.
On the other hand, this bank had identified nearly 6,000 customer cards — almost 5 percent of all cards issued to customers — that had been used at Target stores nationwide during the breach window described by the retailer.
“Nobody has notified us,” my source said. “Law enforcement hasn’t said anything, our statewide banking associations haven’t sent anything out…nothing. Our senior legal counsel today was asking me if we have positive confirmation from the card associations about affected cards, but so far we haven’t gotten anything.”
When I mentioned that a big bank I’d spoken with had found a 100 percent overlap with the Target breach window after purchasing its available cards off a particular black market card shop called rescator[dot]la, my source at the small bank asked would I be willing to advise his fraud team on how to do the same?
CARD SHOPPING
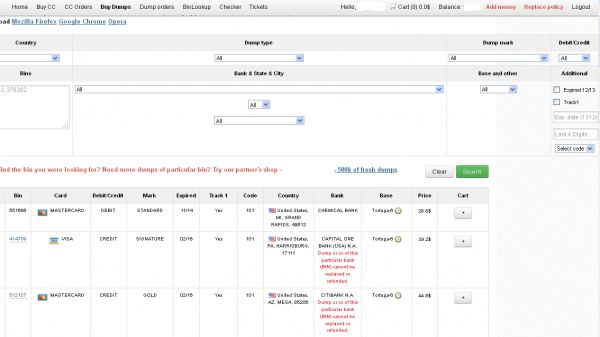
Ultimately, I agreed to help in exchange for permission to write about the bank’s experience without actually naming the institution. The first step in finding any of the bank’s cards for sale was to browse the card shop’s remarkably efficient and customer-friendly Web site and search for the bank’s “BINs”; the Bank Identification Number is merely the first six digits of a debit or credit card, and each bank has its own unique BIN or multiple BINs.
According to the “base” name for all stolen cards sold at this card shop, the proprietor sells only cards stolen in the Target breach.
A quick search on the card shop for the bank’s BINs revealed nearly 100 of its customers’s cards for sale, a mix of MasterCard dumps ranging in price from $26.60 to $44.80 apiece. As one can imagine, this store doesn’t let customers pay for purchases with credit cards; rather, customers can “add money” to their accounts using a variety of irreversible payment mechanisms, including virtual currencies like Bitcoin, Litecoin, WebMoney andPerfectMoney, as well as the more traditional wire transfers via Western Union andMoneyGram.
With my source’s newly registered account funded via wire transfer to the tune of USD $450, it was time to go shopping. My source wasn’t prepared to buy up all of the available cards that match his institution’s BINs, so he opted to start with a batch of 20 or so of the more recently-issued cards for sale.
Like other card shops, this store allows customers to search for available cards using a number of qualifications, including BIN; dozens of card types (MasterCard, Visa, et. al.); expiration date; track type; country; and the name of the financial institution that issued the card.
A key feature of this particular dumps shop is that each card is assigned to a particular “base.” This term is underground slang that refers to an arbitrary code word chosen to describe all of the cards stolen from a specific merchant. In this case, my source at the big bank had said all of the cards his team purchased from this card shop that matched Target’s N0v. 27 – Dec. 15 breach window bore the base name Tortuga, which is Spanish for “tortoise” or “turtle.”
Indeed, shortly after the Target breach began, the proprietor of this card shop — a miscreant nicknamed “Rescator” and a key figure on a Russian-language cybercrime forum known as “Lampeduza” — was advertising a brand new base of one million cards, called Tortuga.
Rescator even created a graphical logo in the Lampeduza forum’s typeface and style, advertising “valid 100% rate,” and offering a money-back guarantee on any cards from this “fresh” base that were found to have been canceled by the card issuer immediately after purchase. In addition, sometime in December, this shop ceased selling cards from other bases aside from those from the Tortuga base. As the month wore on, new Tortuga bases would be added to shop, with each base incrementing by one with almost every passing day (e.g., Tortuga1, Tortuga2, Tortuga3, etc.).
Another fascinating feature of this card shop is that it appears to include the ZIP code and city of the store from which the cards were stolen. One fraud expert I spoke with who asked to remain anonymous said this information is included to help fraudsters purchasing the dumps make same-state purchases, thus avoiding any knee-jerk fraud defenses in which a financial institution might block transactions out-of-state from a known compromised card.
The New England bank decided to purchase 20 of its own cards from this shop, cards from Tortuga bases 6-9, and Tortuga 14 and 15. The store’s “shopping cart” offers the ability to check the validity of each purchased card. Any cards that are checked and found to be invalid automatically get refunded. A check of the cards revealed that just one of the 20 had already been canceled.
The bank quickly ran a fraud and common point-of-purchase analyses on each of the 19 remaining cards. Sure enough, the bank’s database showed that all had been used by customers to make purchases at Target stores around the country between Nov. 29 and Dec. 15.
“Some of these already have confirmed fraud on them, and a few of them were actually just issued recently and have only been used at Target,” my source told me. Incredibly, a number of the cards were flagged for fraud after they were used to make unauthorized purchases at big box retailers, including — wait for it — Target. My source explained that crooks often use stolen dumps to purchase high-priced items such as Xbox consoles and high-dollar amount gift cards, goods that can be fenced, auctioned or otherwise offloaded quickly and easily for cash.
My source said his employer isn’t yet sure which course of action it will take, but that it’s likely the bank will re-issue some or all of the 5,300+ cards affected by the Target breach — most likely sometime after Dec. 25.
The bank is unconcerned that its cards compromised in the Target breach might be used for online shopping fraud because the stolen data does not include the CVV2 — the three digit security code printed on the backs of customer cards. Most online merchants require customers to supply the CVV2 as proof that they posses the legitimate, physical card for the corresponding account that is being used to fund the online purchase.
Update, 5:20 p.m. ET: In a message to consumers, Target CEO Gregg Steinhafel said Target would be offering free credit monitoring for affected customers. Not sure how credit monitoring helps with this specific breach, but at any rate here’s the rest of his statement:
“Yesterday we shared that there was unauthorized access to payment card data at our U.S. stores. The issue has been identified and eliminated. We recognize this has been confusing and disruptive during an already busy holiday season. Our guests’ trust is our top priority at Target and we are committed to making this right.
We want our guests to understand that just because they shopped at Target during the impacted time frame, it doesn’t mean they are victims of fraud. In fact, in other similar situations, there are typically low levels of actual fraud. Most importantly, we want to reassure guests that they will not be held financially responsible for any credit and debit card fraud. And to provide guests with extra assurance, we will be offering free credit monitoring services. We will be in touch with those impacted by this issue soon on how and where to access the service.
We understand it’s been difficult for some guests to reach us via our website and call center. We apologize and want you to understand that we are experiencing unprecedented call volume. Our Target teams are working continuously to build capacity and meet our guests’ needs.
We take this crime seriously. It was a crime against Target, our team members, and most importantly, our guests. We’re in this together, and in that spirit, we are extending a 10% discount – the same amount our team members receive – to guests who shop in U.S. stores on Dec. 21 and 22. Again, we recognize this issue has been confusing and disruptive during an already busy holiday season. We want to emphasize that the issue has been addressed and let guests know they can shop with confidence at their local Target stores.”
Exclusive: More well-known U.S. retailers victims of cyber attacks - sources - Reuters
Target Data Breach Lessons Learned
Target Stores Data Breach
How can you protect yourself from a data breach
Target hack strips banks and credit unions of $200M. By Dara Kerr
23/02/2014 20:09
The widespread security breach reportedly compromised 40 million credit and debit cards, which are costing banks a pretty penny to reissue.

Not only were as many as 110 million Target customers affected by the massive hack on the retailer in December, but banks have also had to deal with the security breach.
The hack is said to have cost banks and credit unions more than $200 million, according to datagathered by the Consumer Bankers Association and the Credit Union National Association. Originally, the two associations estimated that losses tallied around $178 million but now say those costs are rising.
In all, 40 million credit and debit cards were compromised in the breach. So far, banks and credit unions have replaced 54.5 percent, or 21.8 million cards. The cost to banks could increase if additional fraudulent activity occurs with the compromised cards.
The security breach, which yielded the personal information of an estimated 110 million customers, was first identified on December 15. Apparently, cybercriminals accessed customers' private information at point-of-sale terminals during checkout.
Target said the breach occurred between November 27 and December 15 and resulted in the theft of names, mailing addresses, phone numbers, e-mail addresses, and debit and credit card data of people who shopped at the retailer during those dates.
Working to gain consumer confidence in the aftermath of the breach, Target has offered affected customers one year of free credit monitoring and begun development of high-security smart credit cards embedded with microprocessor chips. According to a report earlier this month, the retailer is said to be paying up to $420 million to cover such costs associated with the breach.
Source: https://news.cnet.com/8301-1009_3-57619083-83/target-hack-strips-banks-and-credit-unions-of-$200m/
Insurance Questions, Lawsuits Arise in Wake of Target’s Data Breach - By Young Ha
U.S. retail giant Target Corp. is busy dealing with the aftermath of the massive data breach that exposed account details of some 40 million credit and debit cards.
Already, at least two lawsuits seeking class-action status have been filed against Target. And attorneys general from New York, Massachusetts and Connecticut have contacted the retailer seeking more information about the breach and the steps being taken by Target to protect consumers.
In New York, the state’s Attorney General Eric Schneiderman said there are already reported incidents of identity theft affecting New York consumers.
And according to media reports, these stolen consumer data are already flooding the black market. Credit and debit card accounts stolen from Target’s data breach are being sold on underground black markets for anywhere from $20 to more than $100 per card, reportsKrebsOnSecurity, a security news website.
In such data breach cases, there are several policies that are important for the companies to look at as possible insurance coverages to be triggered, according to attorneys who spoke with Insurance Journal.
Target declined to comment on an inquiry regarding its insurance coverage. But attorneys observed many companies are purchasing insurance coverages to protect against such data breaches.
“A lot of companies are purchasing specialized cyber insurance policies so those have to be examined,” said Joshua Gold, a New York-based attorney and shareholder at law firm Anderson Kill. Gold regularly represents corporate policyholders in insurance coverage matters. Such cyber insurance can be tailored to cover a wide range of expenses, even costs for forensic accounting, credit monitoring, crisis management, notification and setting up call centers to respond to consumer inquiries.
There could also be some measure of protection under traditional policies like the commercial general liability policy, even though finding coverage under traditional policies may be getting increasingly more challenging as the industry continues to add data breach-related exclusions. Most recently, Insurance Services Office Inc. (ISO) filed this year data breach exclusion endorsements concerning its standard-form primary and excess/umbrella commercial general liability policies, to be effective next May.
Commenting on a California lawsuit seeking class-action status, William Um, a policyholder counsel at Hunton & Williams in Los Angeles, said there are allegations that there was a violation of privacy rights. “And those traditional general liability policies will provide that type of coverage and at least trigger the carrier’s duty to defend in that instance,” he said. In the lawsuit, a Target customer in California has alleged invasion of privacy and negligence. (A copy of the complaint is shown at the end of the article.)
“Obviously you need to be mindful of exclusions that are out there. But I would say this falls within the personal injury line of coverage under a general liability policy,” said attorney Um, who has handled a variety of insurance coverage disputes involving class actions, data breach and privacy issues, directors’ and officers’ liability, and other matters. He is not involved in the Target lawsuit.
And based on allegations in the California lawsuit, there is also a potential for coverage under a directors’ and officers’ policy, the attorney said. He observed that the lawsuit appears to include allegations about Target’s failure to act and allegations of “wrongful acts” that would be covered under traditional D&O entity coverages.
In such data breach cases, crime insurance is another possible place to look at, attorney Gold added. “We represented a retailer some time ago and they had a computer hacking breach. We were able to get their insurance coverage for them under a crime policy,” he said.
Defense Costs
As Target grapples with the aftermath of the massive data breach, the retailer could face a lot of expenses incurred for defense costs, Um said. “I think that’s going to be the biggest cost out there because you are going to hire lawyers to defend the lawsuits, and you are going to have to have lawyers out there assisting with the appropriate notifications and responses,” he said.
One question, the attorney said, is whether the plaintiffs in Target lawsuits can manage to overcome what has been difficult in the past — namely, alleging actual compensable damage and getting over the hurdle of showing that individuals have been harmed beyond just their personal information being out in the public.
Um also noted how quickly these lawsuits are getting filed after such incidents occur and how sophisticated the lawsuits have become. He said the California lawsuit was filed on the same day that the media outlets began reporting the data breach.
The lawsuit in California, which was filed in federal court in San Francisco, tries to allege as much damage as possible and with broader allegations, Um said. The lawsuit makes very broad allegations about specific negligent acts on the part of Target, he said.
Technology-Related Claims
Attorney Gold from Anderson Kill also said technology-related insurance claims tend to receive added scrutiny.
“It’s hard to say how each claim is going to be handled because it really does depend upon what insurance policies the policyholder has in place, the circumstances of the loss, and lots of other factors,” he said. But technology-related claims tend to draw added scrutiny from insurance companies, and the more serious the claim, the tougher the insurer could get in paying it, he said.
Gold said he and his firm had cases for policyholders where cyber-specific languages were included into more traditional insurance policies. In terms of the newer, standalone cyber coverages, fights have mostly been “behind the scene” so far, he said.
“I am only aware of one case that’s been litigated involving an actual cyber policy where the insurance company is denying coverage and the policyholder and the insurance company ended up in litigation. I don’t think there has been any meaningful case yet,” Gold said.
Gold also commented on some of the data breach-related insurance cases he has handled in the past. In one case, there was an argument that the data stolen was confidential information and therefore was subject to a policy exclusion.
In another case, an insurer argued that the policyholder’s cyber losses did not directly result from a hacking incident. “So we had a whole fight over what the phrase ‘directly resulting from’ meant in the context of an insurance policy,” he said. “And we obviously didn’t agree with the insurance company’s position, nor did the court. But we still had to go through a very long legal battle over that.”
In yet another case, “a big fight” rose over whether forged wire transfer instructions were covered under a financial institution crime policy, Gold said. “We finally got the insurance company to pay the claim. But these exclusions can get so technical,” he said. “That’s why we always recommend that policyholders really try and understand the insurance policy language that they are going to buy.”
Gold advised, “If you see some fine print in your insurance policy that you can’t understand, it’s much better to try to deal with those issues when you are actually in the process of purchasing the policy, versus having to fight about them later when you have a claim.”
He also offered some general advice for companies that suffer a data security breach. First, companies should start the forensic accounting process right away to ensure the damage is not more widespread than was initially known and to fix whatever security holes that may exist or were exploited by hackers.
Second, companies should do everything they can to comply with state notification laws regarding data breaches, he said.
Third, companies should make sure to give notice to every potentially applicable insurance company. “One thing that can happen is that people understandably are very focused on dealing with the immediate underlying exposure and that is certainly something that is important,” Gold said. “But companies also have to remember they’ve got all kinds of insurance policies that they may need to put on notice.”
“So when in doubt, they should give notice under every potentially applicable policy,” Gold said.
He explained that there is usually very little problem in withdrawing a claim if it turns out the coverage belongs under one policy rather than another. But, on the other hand, if the policyholder gets it wrong and doesn’t give notice under a policy that later turns out to provide meaningful coverage, it could be costly for the policyholder. “Lots of insurance companies will argue that somehow the late notice prejudiced them and somehow void or reduce the insurance coverage that they would otherwise have,” he said.
And if there is an initial denial or some type of reservation from the carrier, the policyholder shouldn’t just accept it, attorney Um said. “Don’t accept the initial denial…[policyholders should] push back,” he said, “and on a going-forward basis, think about these risks as you get into negotiations about policy renewals and the type of policies you want to take a look at.”
Below is a copy of a complaint against Target, filed in the U.S. District Court, Northern District of California: Kirk et al. v. Target Corp., case no. cv 13 5885.
Source: https://www.insurancejournal.com/news/national/2013/12/22/315222.htm
Target Data Breach Highlights Importance Of Insuring Cyber Risks
While cyber risks are sometimes thought of as "online" or Internet risks, a massive information theft recently occurred at Target's brick-and-mortar stores when customers swiped cards and entered PINs while making in-store purchases. On December 19, 2013, Target disclosed that it was the victim of a serious data breach from at least November 27 to December 15 of 2013. More than 40 million debit and credit card numbers were stolen. Hackers stole customer names, card numbers, card expiration dates, the embedded codes on the magnetic strips on the backs of cards, and in some cases PINs for debit cards used at Target.
The card information has reportedly already begun to flood the black market, selling for between $20 and $100 per card. Target has stated that it will offer free credit monitoring services to affected customers.
Specialized cyber risk insurance policies may cover liabilities like those that have inevitably already begun to arise from Target's data breach. Such policies can cover a company's costs of notifying customers of a data breach, offering credit monitoring services, and defense costs and damages for any resulting lawsuits. They may also cover any data or systems lost or destroyed as a result of a hack. Some policies may also cover any resulting loss of revenue, or even damage to a company's reputation following a data breach. Investigations by government agencies targeted at the victim company, such as the Federal Trade Commission or state regulators, may also be covered under cyber risk policies or under a company's comprehensive general liability (CGL) insurance policies.
It is critically important, however, for companies suffering losses like these to position themselves to receive the most coverage. Providing notice to all implicated insurers as soon as practicable, evaluating all available insurance policies, coordinating defense counsel, and communicating with insurers to provide relevant information, are all issues that arise early and must be dealt with swiftly and skillfully to maximize coverage.
Other types of insurance may also come into play. About 40 lawsuits have already been filed against Target. At least one alleges, among other things, that the stolen information constitutes an invasion of privacy. Most CGL policies provide coverage for "personal and advertising injury," which is generally defined to include invasion of privacy claims.
The shareholder lawsuits that usually follow an event like a data breach, alleging wrongdoing by a company's leadership, may also implicate directors' and officers' (D&O) coverage. Some D&O policies, generally those purchased by privately held companies, may also provide "entity" or company coverage for a loss like a data breach as well.
Companies should ensure that their insurance policies are tailored to their specific needs and risks. Having appropriate coverage in place, and seeking guidance from experienced coverage counsel to maximize the funds available, can provide crucial support at a critical time in the event of a cyberattack. Additionally, retaining counsel familiar with navigating cybersecurity issues is essential, both to proactively avoid the risks associated with data breaches and to minimize the impact of an attack after it has occurred.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.